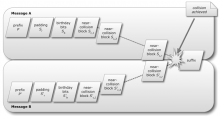
Crypto breakthrough shows Flame was designed by world-class scientists
The Flame espionage malware that infected computers in Iran achieved mathematic breakthroughs that could only have been accomplished by world-class cryptographers, two of the world's foremost cryptography experts said.
"We have confirmed that Flame uses a yet unknown MD5 chosen-prefix collision attack," Marc Stevens and B.M.M. de Weger wrote in an e-mail posted to a cryptography discussion group earlier this week. "The collision attack itself is very interesting from a scientific viewpoint, and there are already some practical implications."