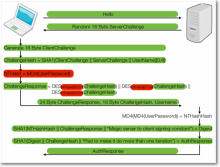
Attack against MS-CHAPv2 puts hundreds of crypto apps at risk
Researchers have devised an attack against a Microsoft-developed authentication scheme that makes it trivial to break the encryption used by hundreds of anonymity and security services, including the iPredator virtual private network offered to users of The Pirate Bay.