Crypto breakthrough shows Flame was designed by world-class scientists
The Flame espionage malware that infected computers in Iran achieved mathematic breakthroughs that could only have been accomplished by world-class cryptographers, two of the world's foremost cryptography experts said.
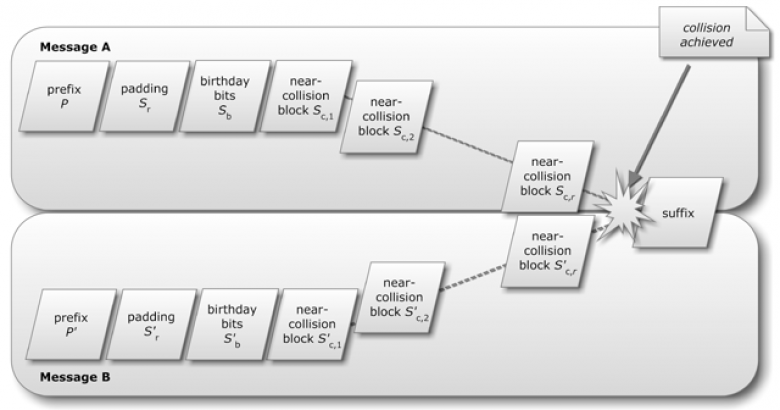
"We have confirmed that Flame uses a yet unknown MD5 chosen-prefix collision attack," Marc Stevens and B.M.M. de Weger wrote in an e-mail posted to a cryptography discussion group earlier this week. "The collision attack itself is very interesting from a scientific viewpoint, and there are already some practical implications."
"Collision" attacks, in which two different sources of plaintext generate identical cryptographic hashes, have long been theorized. But it wasn't until late 2008 that a team of researchers made one truly practical. By using a bank of 200 PlayStation 3 consoles to find collisions in the MD5 algorithm—and exploiting weaknesses in the way secure sockets layer certificates were issued—they constructed a rogue certificate authority that was trusted by all major browsers and operating systems. Stevens, from the Centrum Wiskunde & Informatica in Amsterdam, and de Wegwer, of the Technische Universiteit Eindhoven were two of the driving forces behind the research that made it possible.