Nation state spying malware revealed
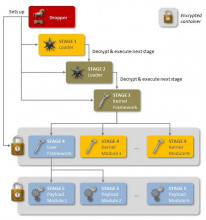
Symantec Security Response has discovered a new malware called Regin which, they say, "...displays a degree of technical competence rarely seen and has been used in spying operations against governments, infrastructure operators, businesses, researchers, and private individuals."
This back-door trojan has been in use, according to the security company, since at least 2008, and has stayed under the radar since.