Malware tricks that you may not know about
There is a constant cat and mouse game between malware, security software companies and computer users, and the chance of one side winning the battle seems slim at best.
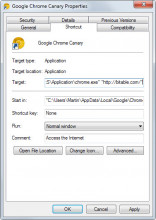
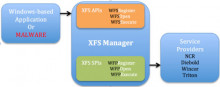
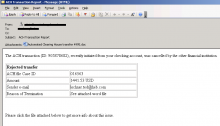
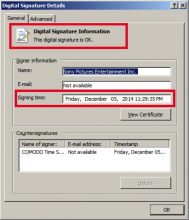
Malwarebytes revealed recently on Malwarebytes Unpacked how Vonteera, a malware previously classified as adware, operates.
While it may not be of interest to many how that particular malware operates, the methods that it uses to infect computer systems and remain on them may very well be as they are used by other malware as well.