Sony attackers also stole certificates to sign malware
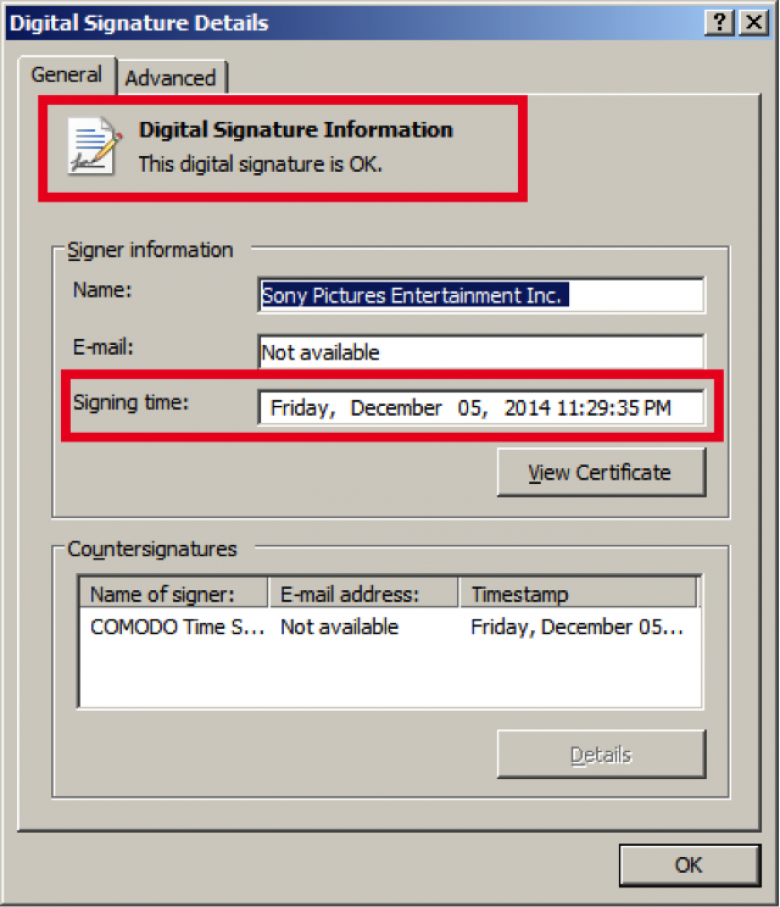
Security firm Kaspersky Labs reports that a new sample of the Destover malware—the malware family used in the recent attack on the networks of Sony Pictures—has been found bearing a valid digital signature that could help it sneak past security screening on some Windows systems. And that digital signature is courtesy of a certificate stolen from Sony Pictures.
The newly discovered variant of the malware was signed on December 5 and is otherwise identical to a version compiled in July. It attempts to connect to two different command and control servers, both previously associated with the malware that took down Sony Pictures—one at a university in Thailand, and another associated with a business customer of Time Warner Cable in Champlain, New York. According to a post by Kaspersky Lab’s Global Research and Analysis Team, the malware alternates attempts at connections between the two IP addresses, pausing between attempts.









































































