Rogue Tor node wraps executables with malware
Josh Pitts of Leviathan Security Group has uncovered a malicious Tor exit node in Russia. The node wraps Windows executable files inside a second, malicious Windows executable. The wrapping is only attempted on uncompressed Windows PE (Portable Executable) files.
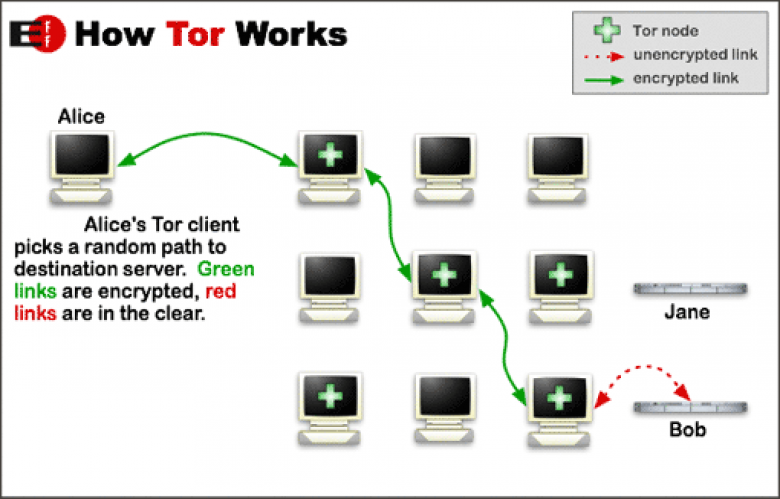
Tor is an anonymizing network which can be used, for good or ill, to hide the source of a request of a server. The recipient of the user request, in this case the site from which a file is being downloaded, would see the exit node as the originator of the communications. At no point in the path of a communication through Tor are both the real source and destination IP addresses unencrypted, and the routes through the Tor network are randomized, making eavesdropping within the network difficult at a minimum.