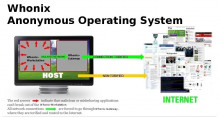
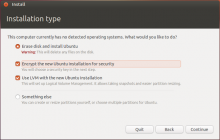
Steelie Neelie admits laptop hack during IGF
Two laptops used by European Commission officials were pinched last week in Azerbaijan's capital Baku during the Internet Governance Forum, Digital Agenda commissioner Neelie Kroes has revealed.
In a blog post at the weekend, Kroes explained that she was in two minds about attending the summit, held this year in the gas and oil-rich country, because the Azerbaijani government has “a very troubling attitude to freedom and democracy”. She added the following: