PGP, TrueCrypt-encrypted files CRACKED by GBP300 tool
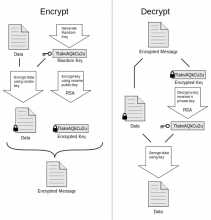
ElcomSoft has built a utility that forages for encryption keys in snapshots of a PC's memory to decrypt PGP and TrueCrypt-protected data.
Forensic Disk Decryptor attempts to unlock information stored in disks and volumes encrypted by BitLocker, PGP or TrueCrypt. The tool is designed for criminal investigators, IT security bods and forensic specialists. PGP and TrueCrypt set the industry standard for whole-disk or partition encryption.