Morto worm phones home over DNS
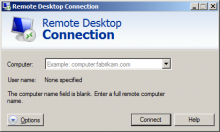
Morto, the first-ever worm to spread via Windows Remote Desktop Protocol (RDP), is not only unique because of its propagation mechanism – it also uses a novel vector, domain name system (DNS) records, to communicate with infected machines, a Symantec researcher said Wednesday.
The DNS is a critical component of internet infrastructure that translates IP addresses into memorable domain names.