Android malware answers calls, eavesdrops on users
Last week, we reported on ANDROIDOS_NICKISPY.A and ANDROIDOS_NICKISPY.B, Android malware that recorded phone calls made from infected devices then sent stolen information to a remote site.
This week, we saw another Android malware with the same code structure as ANDROIDOS_NICKISPY.A. Like the latter, this does not display an icon and executes similar routines, save for some modifications.
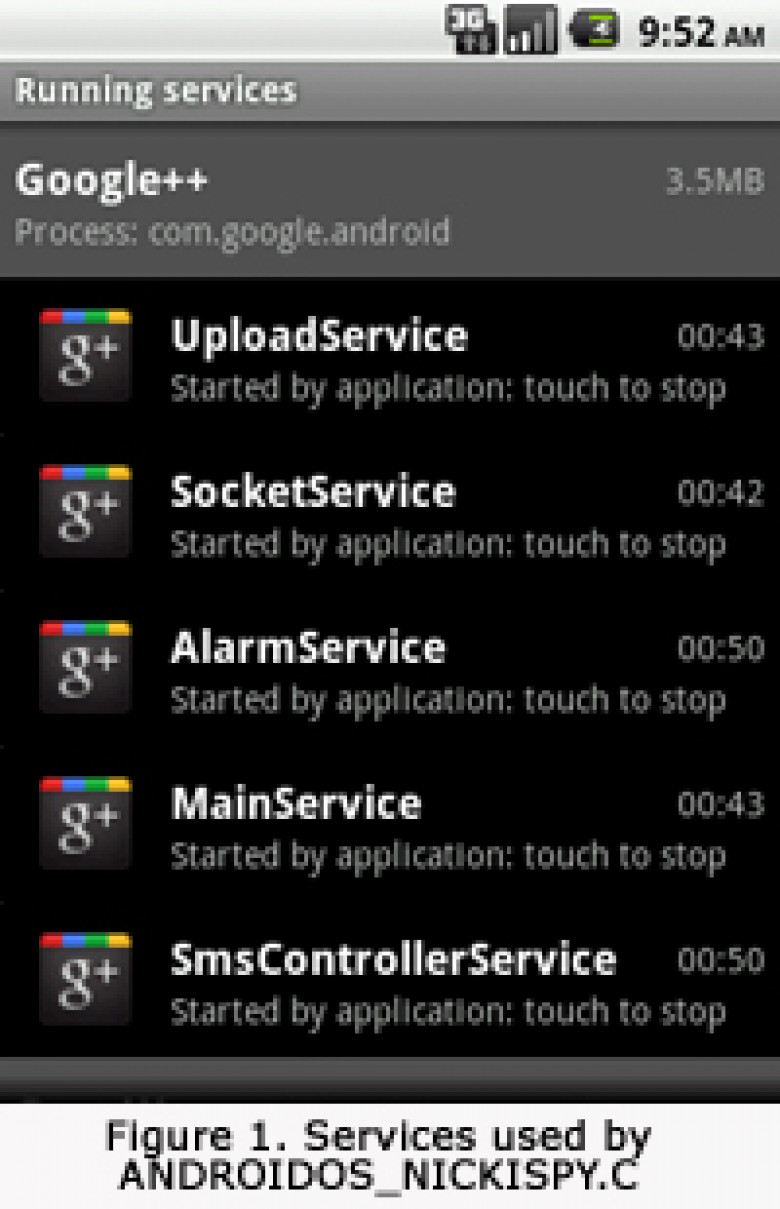
Detected by Trend Micro products as ANDROIDOS_NICKISPY.C, it uses the following services:
- MainService
- AlarmService
- SocketService
- GpsService
- CallRecordService
- CallLogService
- UploadService
- SmsService
- ContactService
- SmsControllerService
- CommandExecutorService
- RegisterService
- CallsListenerService
- KeyguardLockService
- ScreenService
- ManualLocalService
- SyncContactService
- LocationService
- EnvRecordService