Viruses & Malware
AV-TEST Institute evaluates various Android virus scanners
The AV-TEST Institute, an independent anti-virus research provider, inspected 41 different virus and malware scanners for Android specifically testing for detection performance.
According to the report, about half of the scanners are not yet suitable for use mainly due to reliability of detection, with some products scoring a detection rate of less than 65% out of the 680 types of malware tested.
Will the new Microsoft RDP vulnerability spawn Conficker 2.0?
HackLabs director Chris Gatford seems to think that the latest vulnerability discovered in Microsoft's Remote Desktop Protocol could see the birth of Conficker 2.0, as he believes that the scope and impact of the vulnerability is extremely similar to that of MS-08-67.
Discovered in 2008, the vulnerability in Microsoft's Remote Procedure Call affected not only Windows XP, 2000, Vista, Server 2003 and 2008 but also the pre-beta version of Windows 7.
Kaspersky: Duqu Trojan uses 'unknown programming language'
The Duqu Trojan, referred to by some as Stuxnet 2.0, was partly written using an unknown programming language. The payload DLL, which communicates exclusively with the Command and Control (C&C) server so that the worm knows what to do once it has infected a system, has code that doesn’t resemble anything seen before. While secuirty researchers have worked out what the mystery code does, they aren’t sure about the syntax.
Flashback Malware for Mac Changes Infection Tactic
A new variant of the password-stealing Flashback malware aimed at Apple computers has emerged, which tries to install itself after a user visits an infected website, according to new research.
Flashback, discovered by security vendor Intego last September, is engineered to steal passwords for websites, including financial sites. Since its emergence, several variants have appeared showing its authors' innovation.
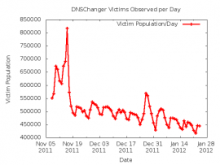
Operation Ghost Click DNS servers to remain online until July
Last year's DNSChanger malware scam was an effort by a small crime ring of Estonian nationals to steal personal information. The scam worked by distributing malware that when installed would change the user's DNS settings to point to the crime ring's rogue DNS network. Since the DNS system is essentially the Internet's phone book, this allowed the crime ring to route seemingly valid Web site URLs to malicious servers.
Symantec finds Zeus infected Aonymous DDoS tool
Considering Anonymous’ disparate nature, and no central authority calling the shots, it’s a surprise this group has not turned on each other already. Antivirus firm Symantec reports that associates of the group are finding themselves victims of denial-of-service software that has been infected by a Trojan horse.
Purported Iran nuke document contains trojan
Targeted attackers are leveraging a patched Adobe Flash vulnerability and the ongoing tension around Iran's suspected nuclear program to spread a difficult-to-detect trojan.
Emails were spreading that contained a Word document titled "Iran's Oil and Nuclear Situation", according to Contagio Malware Dump, a malware sample collection site.
Malware increasingly using DNS as C&C channel to avoid detection
The number of malware threats that receive instructions from attackers through DNS is expected to increase, and most companies are not currently scanning for such activity on their networks, security experts said at the RSA Conference 2012 yesterday.
There are many channels that attackers use for communicating with their botnets, ranging from traditional ones like TCP, IRC and HTTP to more unusual ones like Twitter feeds, Facebook walls and even YouTube comments.
Defeating Hackers and Malware With Disorder
Entropy -- the measure of disorder or randomness -- isn't always desirable in the world of IT security. Kinda, sorta patching your IT systems sometimes, for example, would be a bad thing. At times, though, entropy can be a powerful tool, as in the case of well-chosen passwords that are difficult to crack. A fast-growing SIEM (security incident event managment) company called Vigilant is using entropy in an innovative way that warrants a closer look: Its anomaly-detection service identifies malicious threats based on entropy.