Operation Ghost Click DNS servers to remain online until July
Last year's DNSChanger malware scam was an effort by a small crime ring of Estonian nationals to steal personal information. The scam worked by distributing malware that when installed would change the user's DNS settings to point to the crime ring's rogue DNS network. Since the DNS system is essentially the Internet's phone book, this allowed the crime ring to route seemingly valid Web site URLs to malicious servers.
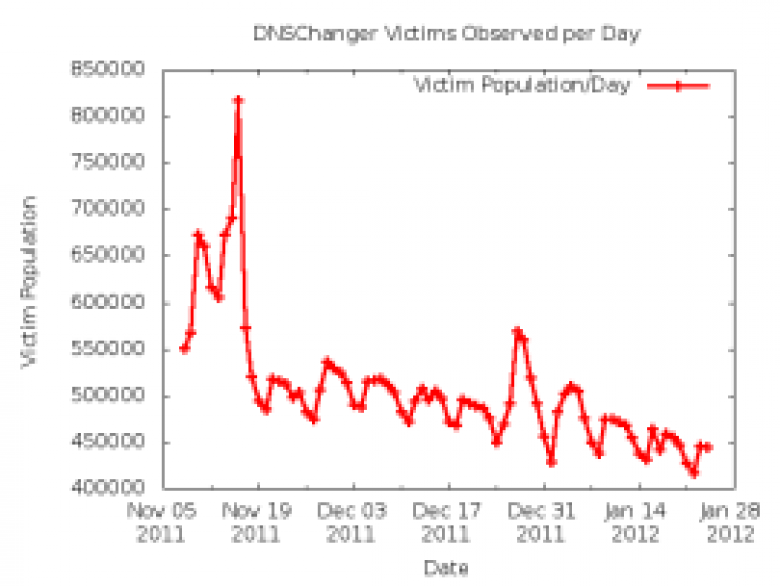
Using this malware, the crime ring was able to get personal information and use it to steal millions of dollars before the FBI's Operation Ghost Click sting resulted in a number of arrests and the seizure of the rogue DNS network. At this point the FBI had the option to destroy the network; however, because many people's DNS settings had been switched to point to this network, the FBI decided to use it to its advantage and turn the stolen servers into valid DNS servers.
This allowed PCs infected with the malware to continue working and accessing the Internet, instead of experiencing sudden outages that could have suddenly affected millions of systems that currently are still infected with the DNS changing malware.