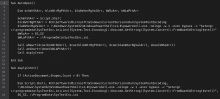
A group that’s been linked to Iranian-based hackers has been working to obfuscate its activities to evade detection, according to new research from Cisco’s Talos researchers.
The hackers, whose attacks are ongoing, are working to avoid host-based signatures and Yara signatures by using a Visual Basic for Applications (VBA) script, PowerShell stager attacks, and a separate command and control server, researchers write in a blog post. In some cases the group, which Talos has dubbed “BlackWater,” has been successful in avoiding detection mechanisms.