New Silex malware is bricking IoT devices, has scary plans
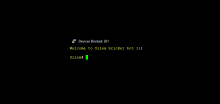
A new strain of malware is wiping the firmware of IoT devices in attacks reminiscent of the old BrickerBot malware that destroyed millions of devices back in 2017.
Named Silex, this malware began operating earlier today, about three-four hours before this article's publication.