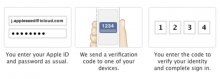
Why you need to enable two-step verification on your Apple ID right now
If you're an iPhone or iPad user (and who isn't?) you probably use iCloud. If you use iCloud, you probably (and should!) use Find My iPhone. If you use iCloud, you probably also use it to sync your email, calendars, contacts and photos between devices. Maybe even Documents and Data too.