LivingSocial hacked: 50m accounts exposed
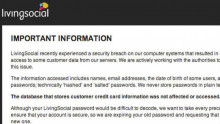
LivingSocial, the second-largest daily deal company behind Groupon, said it was hit by a cyber attack that may have affected more than 50 million customers.
The company said the attack on its computer systems resulted in unauthorised access to customer data, including names, email addresses, date of birth for some users and "encrypted" passwords.