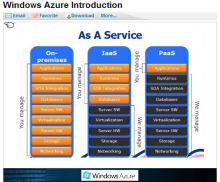
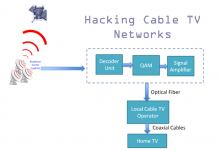
Hacker uses open source to replicate NSA spy tools
Thanks to hacker Michael Ossmann, you can now build gadgets like the National Security Agency uses to intercept communications from the comfort of your own home.
Ossmamnn, a prolific engineer who specializes in wireless Internet security and is widely known for the open source HAckRF, Ubertooth and Dashio projects, was curious about the NSA’s ANT catalog leaked by fugitive Edward Snowden. He decided to do something about it.