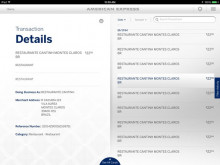
These Are The Hacker Groups That Should Be Keeping You Up At Night
In light of recent hacks, you might be interested in the groups that pose the greatest threats to our cybersecurity.
Ironically, the hacker groups that you should be afraid of also have the least intimidating names. Deep Panda, Putter Panda, and Flying Kitten have been listed by security technology firm CrowdStrike as the groups to watch out for. While they may seem cuddly, these hackers continue to be some of the most dangerous in the world.