Want to beat Microsoft's Windows security defenses? Poke some 32-bit software
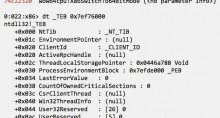
Two chaps claim to have discovered how to trivially circumvent Microsoft's Enhanced Mitigation Experience Toolkit (EMET) using Redmond's own compatibility tools.
A report [PDF] by the duo at Duo Security describes how the Windows on Windows (WoW64) environment can be abused to bypass builtin security tools.