The BAndroid Vulnerability: Why it is serious
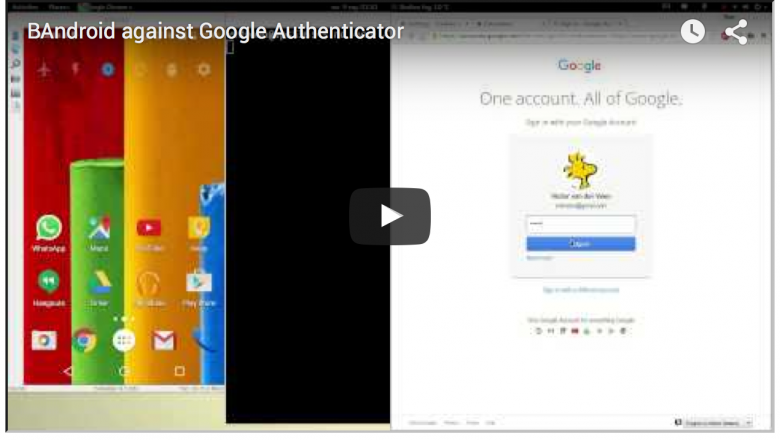
Soon after Dutch newspaper Volkskrant reported [in Dutch] about the Android vulnerability on the 27th of June, some members of the (security) community raised concerns about our attack.
It would be "nothing new" and "overrated". Some people [in Dutch] suggested that having a strong password already helps a lot, while others doubt the possibility of uploading malicious code on the Google Play Store and/or maintain that your phone will display plenty of warnings if you were to try this attack. They all miss the point.
In broad strokes, the scenario is as follows. If attackers have control over the browser on the PC of a user using Google services (like Gmail, Google+, etc.), they can push any app with any permission on any of the user's Android devices, and activate it - allowing one to bypass 2-factor authentication via the phone. Moreover, the installation can be stealthy (without any icon appearing on the screen). For short, we refer to the vulnerability as the BAndroid (Browser-to-Android) vulnerability and to attacks that abuse it as BAndroid attacks.









































































