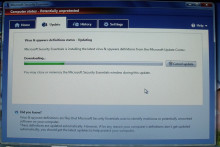
Microsoft opens up new beta program for Microsoft Security Essentials
Microsoft is readying a new public beta program for its popular Security Essentials application.
The software giant has started to send invites to existing Security Essentials 2 beta testers, inviting them to a future test program on Microsoft Connect. The software maker sent the following email: