Computer Virus Stalls an F1 Team's Car Testing
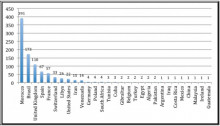
Technology can be wonderful, but sometimes — like when your Mom finds your Twitter feed — it just creates new problems that were previously unthinkable. The latest case in point: On the first day of the second Formula One preseason test, the Marussia team saw its 2014 car complete only three laps around the track because some witless oaf in the team garage downloaded a “Trojan-type virus” onto its computer system. Whoops.