Mystery worm scrambles Iranian databases
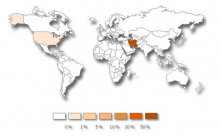
A new worm that appears to be targeted at Iran seeks to sabotage corporate databases by searching for specific phrases and values and replacing them with random ones.
This latest bug, dubbed the "Narilam" worm, goes after Microsoft SQL databases, according to Symantec, which first uncovered the malicious code.