Gameover trojan hides in SSL
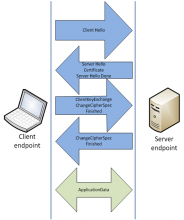
Saboteurs spreading the Gameover banking trojan are using an encrypted secure sockets layer connection to remain undetected and have infected at least a quarter of a million machines.
Researchers at Dell SecureWorks Counter Threat Unit (CTU) detailed attackers' latest schemes to spread the financial malware in a blog post published last Friday.