The Sneaky Simple Malware That Hits Millions of Macs
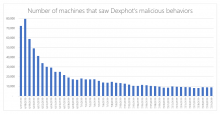
The popular misconception that Macs don’t get viruses has become a lot less popular in recent years, as Apple devices have weathered their fair share of bugs. But it’s still surprising that the most prolific malware on macOS—by one count, affecting one in 10 devices—is so relatively crude.