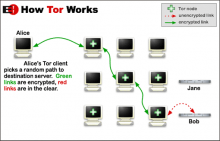
Boffins follow TOR breadcrumbs to identify users
It's easier to identify TOR users than they believe, according to research published by a group of researchers from Georgetown University and the US Naval Research Laboratory (USNRL).
Their paper, Users Get Routed: Traffic Correlation on Tor by Realistic Adversaries, is to be presented in November at November's Conference on Computer and Communications Security (CCS) in Berlin. While it's been published at the personal page of lead author Aaron Johnson of the NRL, it remained under the radar until someone posted a copy to Cryptome.