Critical Remote Code Execution Vulnerabilities Patched by Drupal
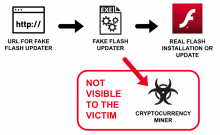
Unpatched versions of the Drupal open source content management system (CMS) are vulnerable to remote exploitation which could lead to remote code execution.
Given enough privileges associated with the user that the Drupal installation runs under, this could allow bad actors to create new accounts with full users rights, as well as view, change, delete data on the compromised target.