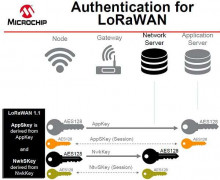
LoRa security greatly strengthened by Microchip Secure Authentication
Microchip is no stranger to security solutions. They began with a Crypto ASIC collaborating with IBM in 1998 and implemented a number of other security solutions over the years culminating in a most impressive Advanced IoT Secure Element solution with their ATECC608A.
At the 2018 MEMS Executive Congress, Cynthia Wright, Principal Cyber Security Engineer, MITRE Corporation presented a call-to-action keynote topic on Cybersecurity (See my article here)