Android Trojan hits 140 countries, 10,000 victims through social media hijacking
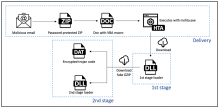
A new Android Trojan has been identified by cybersecurity firm Zimperium, which released a report on Monday explaining how the malware has been able to hit more than 10,000 victims in 144 countries. The trojan -- named FlyTrap by Zimperium researchers -- has been able to spread through "social media hijacking, third-party app stores, and sideloaded applications" since March.