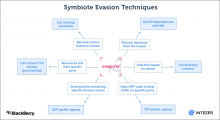
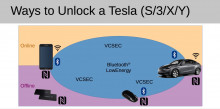
A wide range of routers are under attack by new, unusually sophisticated malware
An unusually advanced hacking group has spent almost two years infecting a wide range of routers in North America and Europe with malware that takes full control of connected devices running Windows, macOS, and Linux, researchers reported on Tuesday.