Use Remote Port Forwarding to Slip Past Firewall Restrictions Unnoticed
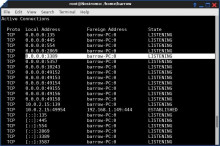
Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.
Remote port forwarding excels in situations where you want access to a service on an internal network and have gained control of a machine on that network via a reverse shell of some kind. Whether you're a pentester or system admin, this is a good thing to know about.