Hackers Deface Network Switches in Russia, Iran with US Flag
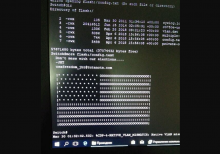
Hackers last Friday disrupted internet access in Russia and Iran with an attack that left a digital message: an image of the US flag accompanied by the words, "Don't mess with our elections."
The messages were written on Cisco network switches, which came under assault from a mysterious hacking group calling itself "JHT."
In an email, the group told Motherboard: "We were tired of attacks from government-backed hackers on the United States and other countries."