What's In Your Water Now? Hackers
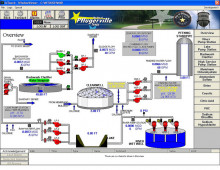
Hackers are known for attacking the computers of banks and government agencies. Now they have a new favorite target: the U.S. water system.
In an unsettling new report on cyber attacks against the nation’s critical infrastructure, the Department of Homeland Security said that water plants were targeted 81 times in 2011, compared with only two incidents in 2010.