The Pirate Bay releases censorship-thwarting browser
The operators of The Pirate Bay, one of the most (in)famous piracy sites on the Internet, have decided to celebrate the site's 10th anniversary by releasing a web browser that allows users to access TPB or other sites censored in their country.
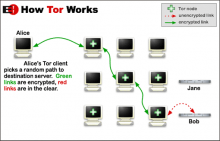
"PirateBrowser is a bundle package of the Tor client (Vidalia), Firefox Portable browser (with foxyproxy addon) and some custom configs," they explained on the browser's official website.