Experts warn fingerprints on iPhone 5S are 'a gift for hackers'
Apple’s fingerprint scanner on the latest iPhone could become a ‘Holy Grail’ for hackers, experts have warned.
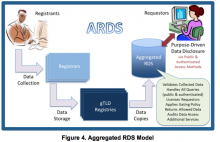
Fingerprint recognition technology on the iPhone 5s captures a permanent biometric feature, German data protection expert Johannes Casper said.
If the ‘secure enclave’ that stores the data in the device’s A7 chip was hacked, thieves would have information about you that does not change, he added. Mr Casper explained: ‘Biometric fingerprints cannot be erased. They are with us for life.