Apple iMessage Research Sparks Corporate Security Debate
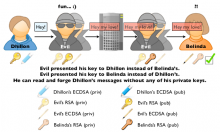
Researchers at the Hack in the Box conference in Kuala Lumpur Thursday showed that Apple on its own or per orders by the U.S. government could harvest messages sent over its proprietary service, which lets people using Apple mobile devices send text messages for free.
Apple has said that its end-to-end encryption prevents the company or anyone else from descrambling the messages. That claim is "just basically lies," Cyril Cattiaux, a developer of iOS jailbreak software and a researcher at Quarkslab, said, as reported by IDG News Service.