Microsoft Mitigates 'Largest Known DDoS Attack'
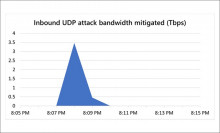
Microsoft successfully mitigated a 3.47 Tbps distributed denial-of-service attack that was targeted at one of its Azure customers from Asia, the company reports in an Azure blog post on DDoS attack trends for Q3 and Q4, published on Tuesday.
This is almost 1 Tbps more than the previous largest DDoS attack, reported in October 2021, which had an attack rate of 2.4 terabytes per second at its peak.