Serious MySQL authentication bypass vulnerability found - Metasploit module already released
A serious security bug in MariaDB and MySQL Disclosed, According to Advisory All MariaDB and MySQL versions up to 5.1.61, 5.2.11, 5.3.5, 5.5.22 are vulnerable. This issue got assigned an id CVE-2012-2122.
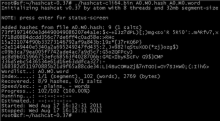
Mysql_hashdump module from Metasploit uses a known username and password to access the master user table of a MySQL server and dump it into a locally-stored "loot" file. This can be easily cracked using a tool like John the Ripper, providing clear-text passwords that may provide further access.