Hackers strike Sotto site ahead of Cybercrime Law's court debate
The official website of Senate Majority Leader Vicente "Tito" Sotto III was hacked by a group claiming to be Anonymous Philippines past midnight on Tuesday, January 8.
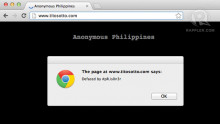
Upon loading titosotto.com users are greeted with a pop-up message that says, "Defaced by #pR.is0n3r." When readers click through, they are greeted by an animated Anonymous Philippines logo, with a message criticizing RA 10175 or the Cybercrime Prevention Act of 2012.