Indonesian hackers protest hacker's arrest ... by hacking
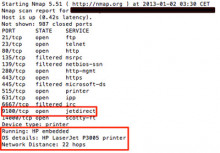
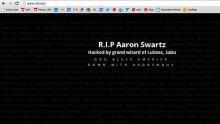
Hackers have been hard at work in Indonesia, defacing web sites left right and center in protest at the treatment of a local hacker who defaced the president’s web site earlier this month and could now face a 12 year jail term.
Internet café worker Wildan Yani Ashari, 22, was cuffed by police last Friday just over a fortnight after he replaced the home page of president Susilo Bambang Yudhoyono (SBY) with the message: “This is a PayBack From Jember Hacker Team”.