Silent Circle moves away from NIST cryptographic standards, cites uncertainty
The U.S. National Security Agency's reported efforts to weaken encryption standards have prompted an encrypted communications company to move away from cryptographic algorithms sanctioned by the U.S. National Institute of Standards and Technology (NIST).
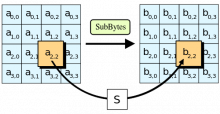
Silent Circle, a provider of encrypted mobile Voice over Internet Protocol (VoIP) and text messaging apps and services, will stop using the Advanced Encryption Standard (AES) cipher and Secure Hash Algorithm 2 (SHA-2) hash functions as default cryptographic algorithms in its products.