Researcher Finds MQTT Hole in IoT Defenses
It started with a simple wish: Martin Horn, security researcher at Avast, wanted a smart home. As he began his research into systems, he found that many devices included set-up instructions with no security provisions. And then, it got worse.
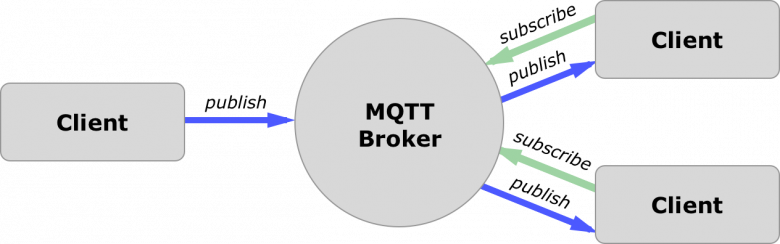
Horn realized that many of the hubs gathering IoT devices into a unified system run Message Queuing Telemetry Transport (MQTT) protocol, an ISO standard for device-to-device communications. And quite a lot of the devices acting as MQTT servers have no security at all. It's not that they use a default user name and password, Horn says, it's that they don't have user names or passwords - period.
"It's not a flaw in IoT devices themselves, it's just a lack of security," Horn says. "In this case, it's wide open, with no password at all." It's important to note, he explains in an Avast blog post, that the MQTT protocol itself is secure, if implemented and configured correctly. The lack of security is the fault of the implementation, not the underlying protocol.