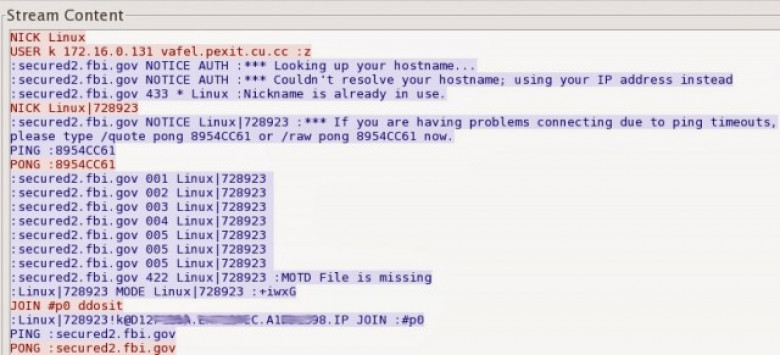
What a successful exploit of a Linux server looks like
Like most mainstream operating systems these days, fully patched installations of Linux provide a level of security that requires a fair amount of malicious hacking to overcome. Those assurances can be completely undone by a single unpatched application, as Andre' DiMino has demonstrated when he documented an Ubuntu machine in his lab being converted into a Bitcoin-mining, denial-of-service-spewing, vulnerability-exploiting hostage under the control of attackers.
A security researcher with George Washington University, DiMino noticed several IP addresses attempting to hijack the Linux server by exploiting a now-patched PHP flaw that gave attackers the ability to remotely execute commands on vulnerable machines. DiMino was curious to know what the people behind the attacks intended to do with his machine, so he set up a "honeypot" box that, for research purposes, ran an older version of the Web development language.
The attackers' HTTP POST request contained a variety of commands that in short order downloaded a Perl script that was disguised as a PDF document file, executed it, and then deleted it. To ensure success, the attackers repeated the steps using curl, fetch, lwp-get requests. The Perl script was programmed to sleep for periods of time, presumably to prevent administrators from noticing anything amiss. Eventually, the compromised machine connected to an Internet relay chat channel, where it downloaded another script and executed it. Then he ran forensic software and snapped lots of screen shots so everyone could follow along.