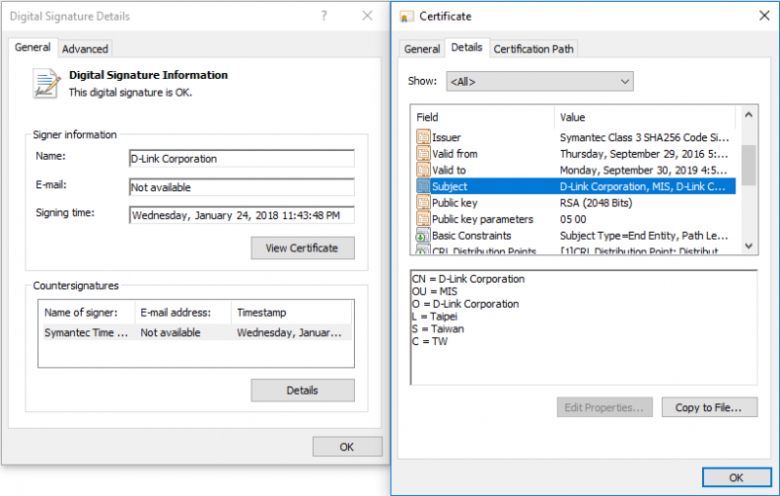
Stolen certificates from D-Link used to sign password-stealing malware
Criminals recently stole code-signing certificates from router and camera maker D-Link and another Taiwanese company and used them to pass off malware that steals passwords and backdoors PCs, a researcher said Monday.
The certificates were used to cryptographically verify that legitimate software was issued by D-Link and Changing Information Technology. Microsoft Windows, Apple’s macOS, and most other operating systems rely on the cryptographic signatures produced by such certificates to help users ensure that executable files attached to emails or downloaded on websites were developed by trusted companies rather than malicious actors masquerading as those trusted companies.
Somehow, members of an advanced persistent-threat hacking group known as BlackTech obtained the certificates belonging to D-Link and Changing Information Technology, the researcher with antivirus provider Eset said in a blog post. The attackers then used the certificates to sign two pieces of malware, one a remotely controlled backdoor and the other a related password stealer. Both pieces of malware are referred to as Plead and are used in espionage campaigns against targets located in East Asia. The Japan Computer Emergency Response team recently documented the Plead malware here. AV provider Trend Micro recently wrote about BlackTech here.