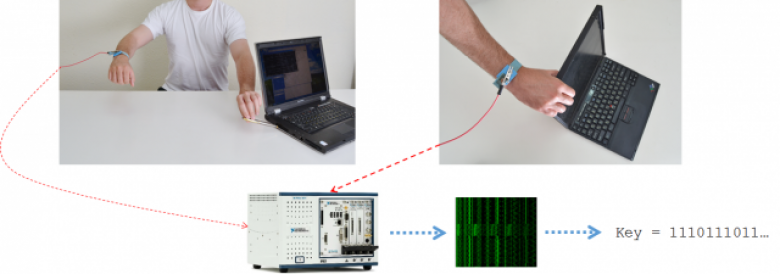
Stealing encryption keys through the power of touch
Researchers from Tel Aviv University have demonstrated an attack against the GnuPG encryption software that enables them to retrieve decryption keys by touching exposed metal parts of laptop computers.
There are several ways of attacking encryption systems. At one end of the spectrum, there are flaws and weaknesses in the algorithms themselves that make it easier than it should be to figure out the key to decrypt something. At the other end, there are flaws and weaknesses in human flesh and bones that make it easier than it should be to force someone to offer up the key to decrypt something.
In the middle are a range of attacks that don't depend on flaws on the encryption algorithms but rather in the way they've been implemented. Encryption systems, both software and hardware, can leak information about the keys being used in all sorts of indirect ways, such as the performance of the system's cache, or the time taken to perform encryption and decryption operations. Attacks using these indirect information leaks are known collectively as side channel attacks.