Mystery malware that targeted energy group contains amateur coding goof
The mystery malware that recently wreaked havoc on energy sector computers contains an amateur programming error that's not typical of state-sponsored attacks, security researchers said.
The flaw, which was reported in a blog post published on Tuesday by researchers from Russia-based Kaspersky Lab, was found in "Shamoon," a piece of malware that wipes data from infected computers and also prevents them from booting up. It struck computers in at least one organization tied to the energy industry. After the word "wiper" was found embedded in the underlying binary, some researchers questioned whether the malware was linked to an earlier attack by that name that was used to destroy data belonging to Iran's oil ministry.
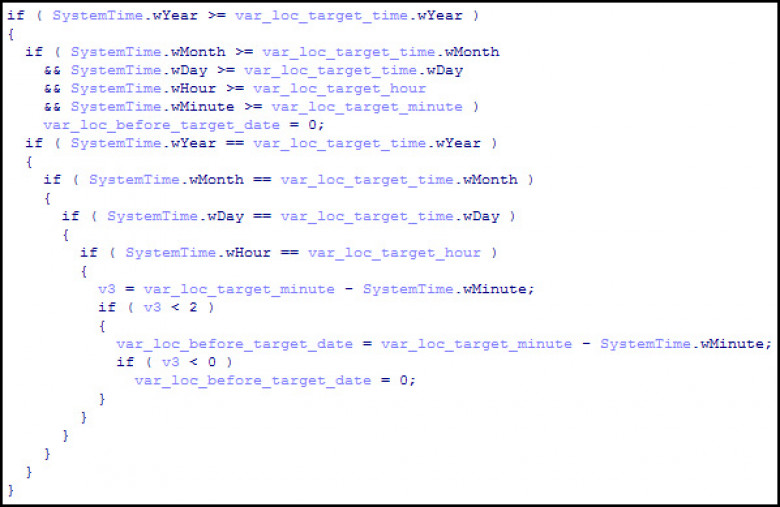
Kaspersky researchers later dismissed those suspicions after finding significant differences in the way the two pieces of malware behaved. Kaspersky's post on Tuesday introduced yet more evidence that Shamoon wasn't state sponsored: a programming routine that fails to accurately determine if a specified date has come. The date hard-coded into the malware is August 15, 2012. If the month of the current date falls in 2013 or later, but the calendar month is earlier than August, the malware treats the date as coming before the August 2012 checkpoint value. The flaw is the result of corrupted logic.