How GitHub handled getting hacked
GitHub was hacked today in a way that exposed every repository. Russian hacker Egor Homakov discovered a public key form update vulnerability that allowed him (or anyone else, for that matter) to access any GitHub repository with full administrator privileges. As a result, anyone could, for example, commit to master, reopen and close issues in Issue Tracker, or even wipe the entire history of any GitHub project.
This was possible because of how Rails handles mass assignment of attributes (see Enlight Solutions). In short, if developers don’t protect against mass assignment, it means that a malicious user can set any value in your models. GitHub has since fixed this vulnerability, but the way the company handled the event is, unfortunately, the real story.
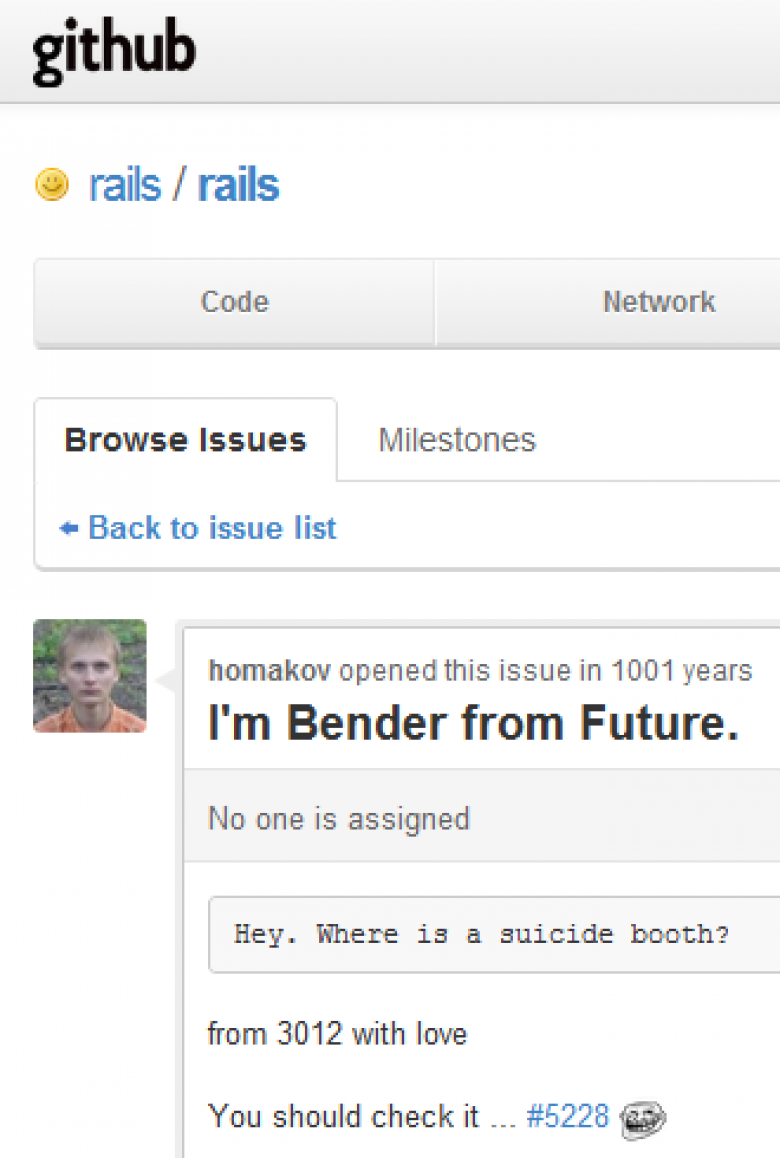
Let’s take a look at what happened this week, as well as today’s culmination. It all started when Homakov opened an issue in the rails repository on GitHub titled “Mass assignment vulnerability - how to force dev. define attr_accesible?” The majority of Rails applications are likely vulnerable, but Homakov’s issue was closed multiple times and he reopened it again and again to try to get his point across.