Apple's iCloud protocols cracked and analyzed
Smartphones carry a lot of sensitive data that in theory should be accessible only to their owners. In practice, a lot of it can be exfiltrated from the devices and from the backups either stored on the device or in the cloud by employing different forensic methods.
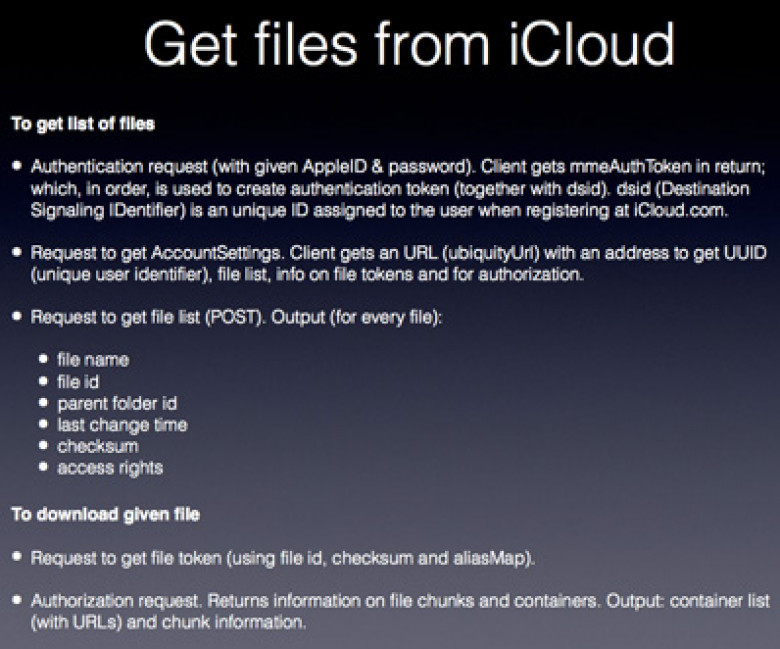
In his presentation at the Hack in the Box Conference, co-founder and CEO of Russian password-cracking / recovery company ElcomSoft Vladimir Katalov has shared the results of their efforts in cracking and the discoveries they made by analysing Apple's iCloud protocols, as well as those used for Windows Phone and BlackBerry backups.
First he showed us a short overview of the forensic methods that can be used on devices running one of the four leading mobile operating systems. Different methods are applicable to different devices. For example, BlackBerry does not offer the option of cloud backup or the option of allowing users to locate lost or stolen phones, so that information obviously can't be accessed in the cloud.