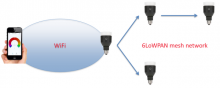
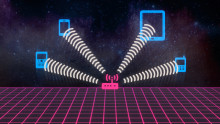
GoTenna creates a cell network out of thin air anywhere on Earth
Our modern, wired society often romanticizes going off the grid. Pack-toting hikers bravely venture into areas without electricity or -- gasp! -- cell service, unfortunately inhibiting the posting of that picture-perfect Instagram shot.